Cybersecurity is a hot-button issue for many in the C-suite following recent high-profile data breaches, but the conversation about data security needs to shift from worrying about vulnerability to include the internal management, storage and use of data in ways that will limit exposure and harm to end customers in the event of a breach.
The conversation about data security and the risks of theft, exposure, and other cyber risks has been a hot topic of water cooler chats. Questions such as how secure is our data, what do we need to consider in our IT strategy to protect our (and our client’s) data, and how do we mitigate the risks are just the tip of the data security iceberg.
There is an oft-ignored reality about the relationship between cybersecurity and data that needs to be considered in any IT strategy, and that is this: security is more than a secure perimeter. Cyber security has long been a concern for boards and the c-suite – who are grateful it’s not their organisation in the news – and perhaps a greater concern for those who are managing through a data breach.
However, as cyber incidents are on the rise, up 13% on 2021-22 according to the Australian Cyber Security Centre, one striking thing is how tough it can be for risk mitigation data projects to get approval. Without the intrinsic ROI that product or service projects can deliver, standing up a data hygiene project that reduces risk, improves security, and reduces the potential cost of dealing with a hack can be harder to get across the approval line.
As specialists in the data space – not cybersecurity – we thought it worth exploring what organisations can do to mitigate the risk of what’s inside the perimeter to help cyber specialists do their best to defend it.
Consider this: It’s not if a hack will occur but when
The 2022 ACSC Annual Cyber Threat Report (July 2021-2022) makes for some sober reading, as more than 76,000 cybercrime incidents were reported in that financial year, up 13 percent on the previous year and equating to a report every 7 minutes. Not all of these are for large organisations that make the headlines, but they are devastating nonetheless for individuals whose data is exposed.
As the attacks are increasingly sophisticated and more frequent, it may be inevitable that an organisation will be hacked. While we obviously can’t say that categorically, the odds indicate it’s not a matter of if but when a hack might occur.
Data is a valuable business asset. However, there are many types of data within a perimeter that organisations need to consider. With that as context, organisations need to consider what sort of data they hold, how they hold it, and why they hold onto it. It’s also important for the risk mitigation conversation that will help ensure hygiene projects can de-risk their exposure.
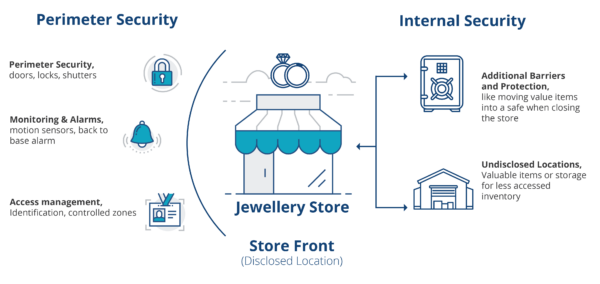
Perimeter security vs internal security
Let’s consider a simple jewellery store as an example.
By the nature of the business, a jewellery store will hold highly valuable goods that will have several protections to prevent a break-in. They will reinforce the perimeter of the store with doors, locks, and alarms, perhaps monitoring systems and alarm systems, should the perimeter be breached.
But they don’t leave those valuables lying around. To limit the damage and loss that could occur in the event of a break-in, additional measures are taken, such as:
- Valuables are securely locked away onsite if needed the next day or taken offsite to undisclosed locations if not
- Inventory is managed; for example, does a jeweller need to store all diamonds for production in the known, disclosed shopfront location or only what’s needed for repairs or customer orders that day?
Valuable data is no different
Data serves many purposes for organisations, and valuable data is no different to jewellery when you think about it.
Let’s assume that the organisation has taken steps to ensure that robust perimeter security is in place. What else should be considered as part of mitigating the potential damage of a breach, which might include data theft, data exposure on the dark web, or resulting reputational damage?
There will be valuable data used day-to-day to run the business but consider your static data and legacy applications. There is often significant overlap between the two and tension between the need to retain access to static data vs the often-significant cost for upgrades and moving out legacy applications. The cost-benefit challenge is that the cost of maintaining those systems often outweighs the static data that is retained in those systems.
What is static data?
Static data is data that organisations retain, knowingly and unknowingly, for many reasons. It’s static because it may not be involved, used, or updated for operational purposes or required day-to-day to deliver products and services to customers. It may be retained to ensure compliance with legal obligations or because of internal policy to retain records to certain time periods or a lack of policy which often results in retaining everything.
What is a legacy application?
A Legacy application is, in overly simple terms, outdated. That doesn’t mean it isn’t fit for purpose or doesn’t work, it just means there are new versions or options available, that might not be as cost-effective or provide a present is due to its age, it makes no longer be supported by security patches and updates, and it may present known and yet-to-be-known vulnerabilities that can be exploited.
How to overcome the cost-benefit challenge
There are two questions to ask: first, does the organisation really need the static data, and second, is a legacy application the best place to store and access that data?
Upon review, static data typically falls into three categories.
- Require: Static data that is necessary to operate.
- Retain: Static data that must be kept, typically for legislative reasons.
- Purge: Static data neither of the above and potentially purgeable.
In the world of big data, there is an underlying assumption that the more data the better, which can in some ways be true, but all data, particularly sensitive and personal identifiable data starts to present a great risk when held without any end date.
Record retention policies and compliance rules can sometimes be difficult to implement depending on the systems they are stored in, which can sometimes mean they do not get applied and we store more than we need to.
It may also be a matter of the use case. For example, if keeping all customer data going back decades is done to understand the customer behaviours across its lifetime, do we need to know if Joe Bloggs with licence number 123 still lives at the same address or do we need to know customer A of gender X lived in suburb Y over Z years? In this example, it’s the pattern of customers that is important, not the individual customer themselves.
Lastly, accessing that data via a legacy application that may not have had the latest patches and updates or is no longer supported with patches and updates can present serious vulnerabilities and provide easy access to any and all types of data once the perimeter is breached.
Upgrading every application to the latest and greatest is often cost-prohibitive. Instead, application archiving solutions can provide a more cost-effective alternative that allows access to retained data regardless of its form (structure, documents etc). It can be offset by licence, storage, and computational costs associated with storing data in legacy applications and remove the associated vulnerabilities at the same time.
The appeal of application archiving solutions is that they go further than data security; this approach also removes legacy applications to simplify an organisation’s IT architecture and potentially lead to reducing costs in future projects. They are often also more cost-effective and efficient to support.
The right solution can also improve security by more easily applying data retention policies and encryption for key data that may not have been so easily done in the legacy application.
Make it harder to do serious damage and limit the losses
While good hygiene projects (link) are often hard to get across the line, no organisation wants to have to respond to a breach or bear significant financial or reputational costs. Perhaps, however, making it much harder to find data worth stealing is worth the pre-emptive investment.
Quay Consulting partners with the CPM Group to enable organisations to adopt better systems integration as part of the project delivery process. To find out more, please contact us.
We believe that quality thought leadership is worth sharing and encourage you to share with your colleagues. If you’re interested in republishing our content, here’s what’s okay and what’s not okay.